Reducing IoT & Cloud Risk in HealthTech
Ramping teams up with the right training blend
Cloud migration is happening fast across most businesses. For this growing healthcare company, what once could be handled by the InfoSec team became problematic as more lines of business accelerated cloud adoption. Additionally, recent attacks on Healthcare Devices fueled the need to build and maintain secure software.
To up-level skills in an engaging way, a blend of self-paced courses and hands-on cyber ranges was the solution.
Getting to the Payoff: A Complex but Achievable Task
Like many organizations, disparate groups handled security differently. Some utilized DevOps, others had hybrid IoT/ cloud deployments and all were struggling to secure APIs.This common scenario creates risk if not addressed holistically.
This company had added complexities including:
Above all, management sought a phased approach that would enable attainment of short-term goals without
overwhelming teams in the process.
The training plan included role- and technology-specific learning paths for the development, operations, and security teams. Those paths were complemented by real-time assessments on cyber range technology environments that provided valuable insight into how each team was progressing.
The Journey to Healthcare Cloud Security Excellence
1. Build Cloud & IoT Security Awareness
PURPOSE – Ensure security basics (including DevOps) are understood across teams.
HOW – CBT courses applicable to all roles and responsibilities
- Fundamentals of Application Security
- Fundamentals of Secure Cloud Development
- Fundamentals of DB Security
- Fundamentals of DevSecOps
- OWASP IoT Top Ten
- Meeting Cloud Governance Requirements
2. Benchmark Skills
PURPOSE – Baseline against industry standards, set goals for outcomes, and design individual learning paths from results.
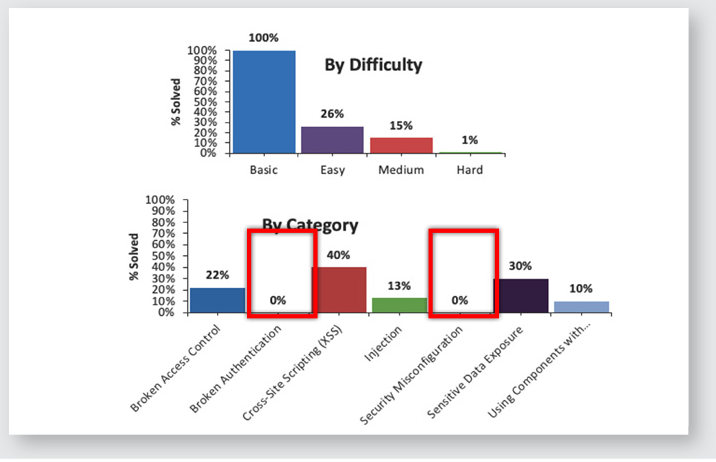
HOW – ShadowBank cyber range, a fully-featured Web application with poorly implemented security principles and vulnerabilities. Detailed reports baselined staff risk, described next steps, and tracked against goals.
3. Milestone – Status Check
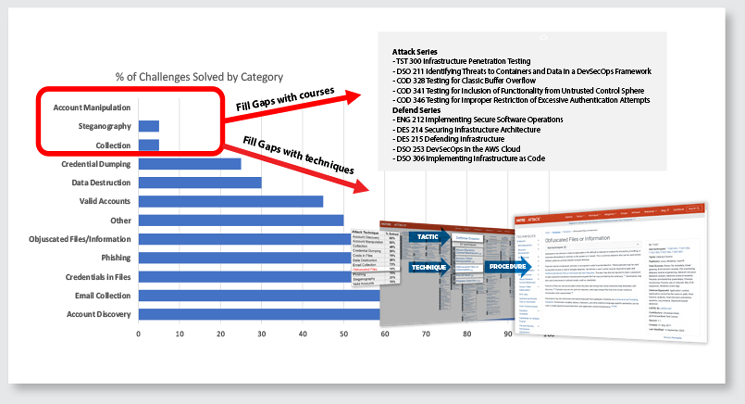
Driven by cyber range performance and target goals, learning paths were tweaked. Those needing deeper expertise moved on to specialized training.
4. Build Specialized Skills
PURPOSE – Ensure staff can conduct security activities specific to their job function and tech stack. This is critical to engagement and knowledge retention – a ”one size fits all” approach would not yield the desired results.
HOW – Role- and technology-specific courses:
Developers
|
Operations/IT
|
Architects
|
InfoSec
|
5. Elevate Expertise with Cyber Ranges
PURPOSE
Move towards cloud security excellence by further honing the skill sets to bring specific teams to elite status utilizing organizational and industry benchmarks.
HOW
Role-based cyber range play
6. Milestone – Optimization

Advanced & Sustained Training: Continuing to Pay Dividends
With a concerted and well-executed security training program, this company was able to quickly overcome critical skills gaps, align to industry frameworks, and zero in on the exact role-based security training requirements across disparate groups. Overall, this approach has greatly reduced the company’s risk profile for cloud and IoT security.
Additionally, they recognized that security wasn’t a ‘one and done effort. Phase 2 includes expanding to a larger audience, focusing on data privacy, and aligning with ISO.