CASE STUDY: METACASH
PREVENTING PHISHING ATTACKS
AGAINST SMART CONTRACTS IN BLOCKCHAIN APPLICATIONS
Blockchain Adoption Challenges:
Price Fluctuation and Transaction Fees
Cryptocurrencies have been slow in their goal to reach mass adoption, in part due to the inherent price fluctuations to the underlying crypto assets. It is easy to see why someone may not want to spend their currency on goods and services if they think the value of the currency will rise by simply waiting.
To combat this, blockchain platforms have converged around the concept of stable coins as a means of exchange. These tokens are mapped 1-to-1 with a stable national currency like the US dollar through various technical mechanisms. This allows users to achieve the benefits of conducting business on a blockchain platform, such as lower fees and the minimization of rent-seeking middlemen, without the risk of holding on to an unstable form of money.
The Ethereum blockchain is the most popular public smart contract platform at the time of writing and has many stable coins built on top of its network. Unfortunately, due to the design of the system, all transactions that are made to the blockchain must pay a small transaction fee in the blockchain’s native currency, Ether. This presents a conundrum for mass adoption. Users that want to achieve simple, fast, low-friction payments without needing to understand any of the underlying blockchain techs can send stable coins easily over the Ethereum network; however, they must still purchase Ether to cover the cost of fees, increasing the friction for onboarding new users.
Blockchain Adoption Solutions:
Stable Coins and Relay Networks
Metacash is a project that aims to solve this problem by creating a network of relayers that will pay your transaction fees for you. By signing a message authorizing a stable coin transaction, a relayer can submit a transaction to the Ethereum network on behalf of the user that transfers the stable coin from that user’s Metacash wallet for them. With this system, the relayer can pay all the transaction fees using their personal Ether and collect small payments from the user’s wallet in their stable coin.
Signing a transaction or message with the user’s private key is the only way to move funds from their wallet. If relayers become unavailable or act malicious, the user will still have full control of their funds. This allows users to interact with the growing blockchain ecosystem in a safe manner, using only stable coins and not exposing themselves to volatility or confusion when dealing with other crypto assets.
Security Innovation Assessment:
Phishing Threats to Message Signing
Security Innovation approached Metacash shortly after the initial release of their beta contract after identifying a possible threat to their design. Due to the way many Ethereum wallets sign messages (using the eth_sign web3.js function), it is difficult for users to verify what their signed message does or ensure that the message is only used in the intended smart contract. By default, wallet interfaces will just display a blob of hex data to be signed with no context whatsoever.
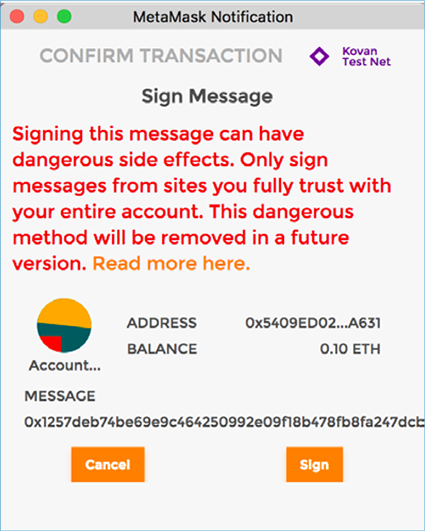
Example UX of signing a message with “eth_sign”
source: http://eips.ethereum.org/EIPS/eip-712
This issue presented a unique challenge for Metacash. Let’s assume there is a malicious DApp (Decentralized application that interacts with a smart contract) called CryptoBullDogs. This DApp might have a feature that requires a user to sign a message with their wallet in order to perform a standard operation, such as registering or authenticating to the DApp. Despite seeing potential warnings, a user is likely to sign the random hex data if this is the user experience that they are used to with other DApps.
This issue is similar in nature to the risk of self-signed certificates in web 2.0 applications. If a user becomes accustomed to clicking past the warnings for their internal company tool, they are more likely to ignore the warning in a legitimate Man-in-the-Middle attack.
Once the user has signed the message, Crypto-BullDogs can collect the signed message and replay this to a Metacash relayer. Depending on what malicious message CryptoBullDogs has tricked the user into signing, they may be able to steal all the funds stored in the user’s Metacash wallet.
“\x19Ethereum Signed Message:\n32”
Prefix used by Metacash wallet & smart contracts:
“\x19Metacash Signed Message:\n32”
Addressing the Signing Issues
Security Innovation worked closely with Metacash to identify remediation options for this issue. Our top recommendation was for Metacash to implement the EIP 712 structured signed data standard. This standard is a current work in progress that is an active development among major wallet software and libraries. It provides clear UI indications of the “domain” that the signed message is for, as well as details about the parameters being signed. That way the user can clearly see that CryptoBullDogs is signing a message intended for Metacash and will reject it.
While EIP 712 is a promising solution to this problem, it is an incomplete standard and general-purpose libraries are far from finalized. After discussing alternative solutions with Metacash, we concluded that the risk of this issue could be minimized by ensuring users only use the official Metacash wallet software with their Metacash wallets and not with other DApps.
This solution remains compliant with the EIP-191 Signed Data Standard since the version byte ‘M’ (0x4D) has not been allocated and ensures that any signed message produced by a malicious DApp will be incompatible with the Metacash smart contracts and cannot be used to steal funds.
The developers of Metacash were able to come up with an elegant solution to this issue where the prefix string to a signed message would differ in the Metacash wallet and smart contracts than that produced by the generic eth_sign function.
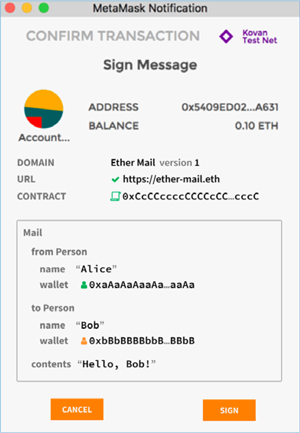
Additional Security
Security Innovation additionally performed a full smart contract audit of the second version of the Metacash smart contracts. In total, 10 security issues were identified, with 2 being ranked high severity that could result in a loss of user funds or theft. Metacash was able to review and respond to each of the findings and patch the issues in their latest release of the contract. “The report from Security Innovation has really impressed us,” says Nour Haridy, lead architect of the Metacash project. “Some issues that were raised could have been completely catastrophic if exploited. We are grateful to have partnered with the engineers at Security Innovation to amplify the security of our code and protect our users’ assets.”
We at Security Innovation are very excited to support projects like Metacash that seek to bring usability and adoption to this exciting new technological landscape. The full Metacash Smart Contract Audit Report can be found here: http://bit.ly/metacash2019.





