Comprehensive Cybersecurity Solutions Tailored to Protect Your Technology Wherever it Operates
Security Innovation delivers precise, actionable security services to safeguard your Web, Cloud, AI, IoT, Mobile, Desktop, and more—seamlessly integrating protection into your development and operational processes.
Security Innovation provides comprehensive cybersecurity consulting that empowers organizations to protect their software at every stage. From development and deployment to ongoing operations, we specialize in delivering precise, actionable security solutions that eliminate false positives and streamline risk mitigation. With decades of expertise, we integrate world-class security seamlessly into your solutions.
Comprehensive
Security Solutions for
All Environments

Safeguard every aspect of your software lifecycle—spanning Web, Cloud, IoT, Mobile, and Desktop technologies.
Services include penetration testing, secure code reviews, secure SDLC assessments, and cloud configuration reviews.
Precision-Driven
Actions and Zero
False Positives

Go beyond automated scans with precision-driven analysis, providing clear remediation recommendations and eliminating security noise.
Swift, actionable insights from experienced security experts ensure comprehensive protection for your software.
Trusted
Expertise
Since 2002

As pioneers in software security, Security Innovation leverages two decades of deep experience to fortify your software against modern threats.
Our team integrates with your development, engineering, and operations teams to ensure robust security throughout your entire software lifecycle.
WHETHER FORTUNE 100 OR SMBs, WE’VE HELPED ORGANIZATIONS PROTECT THEIR BRAND








SECURE YOUR SOFTWARE AND ECOSYSTEM
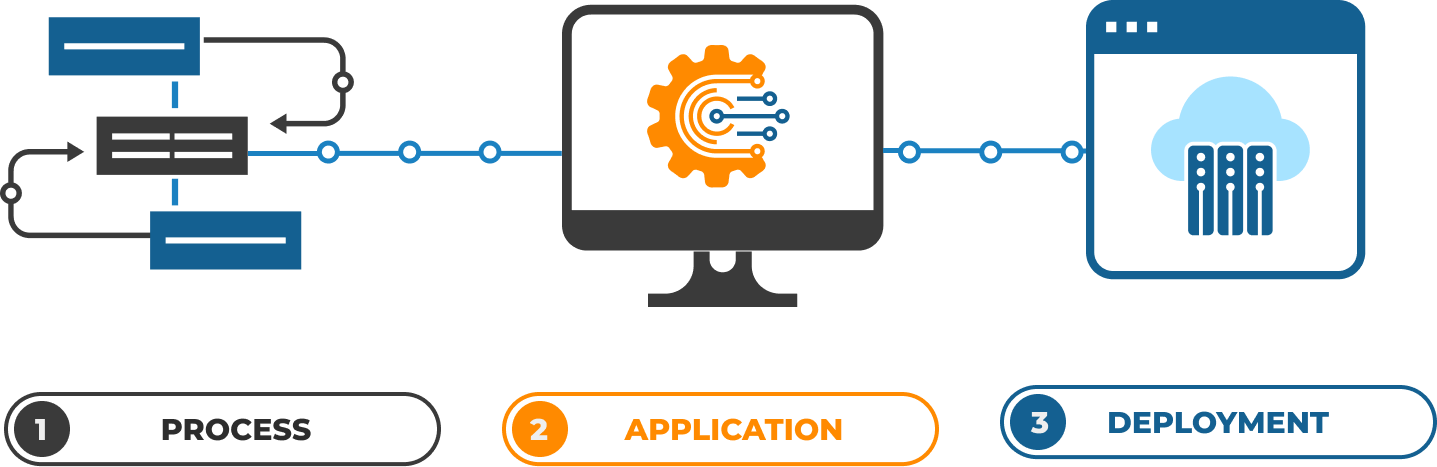
SDLC
SECURE AT THE SOURCE
Stop dangerous practices and release with confidence
API • CODE • DESIGN
SECURE AT RELEASE
Fix vulnerabilities at design, code and production level
API • CODE • DESIGN
SECURE IN PLAY
Harden configurations, controls and services
Service Offerings Overview:

PENETRATION TESTING
Uncover and address vulnerabilities across web, mobile, IoT, and cloud environments through exhaustive simulated real-world attacks, ensuring resilient security for your systems.

SECURE CODE REVIEW
Go beyond automated scans with manual, expert-led secure code reviews that pinpoint vulnerabilities and provide detailed remediation guidance to eliminate exploitable flaws.

CLOUD CONFIGURATION REVIEW
Secure your cloud environments by identifying and mitigating configuration errors, optimizing security protocols across platforms such as AWS, Azure, and Google Cloud.

SECURE SDLC & SECURE ARCHITECTURE ASSESSMENTS
Embed security into every phase of your software development lifecycle through risk assessments, secure architecture reviews, and secure coding practices.
CYBERSECURITY INCIDENT RESPONSE TABLETOP EXERCISES
Prepare for real-world cybersecurity threats with scenario-based tabletop exercises designed to improve your organization’s threat response capabilities












